<--- Back to Details
| First Page | Document Content | |
|---|---|---|
 Date: 2014-12-16 19:06:23A5/1 GSM SMS Keystream Um interface IMSI-catcher Stream ciphers Technology Mobile technology |
Add to Reading List |
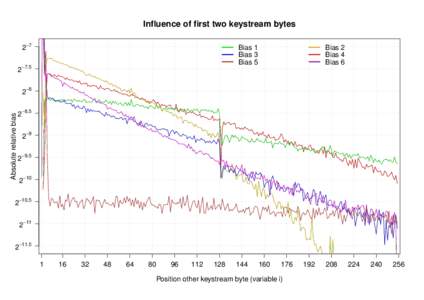 | Influence of first two keystream bytes 2−7 Bias 1 Bias 3 Bias 5DocID: 1xV86 - View Document |
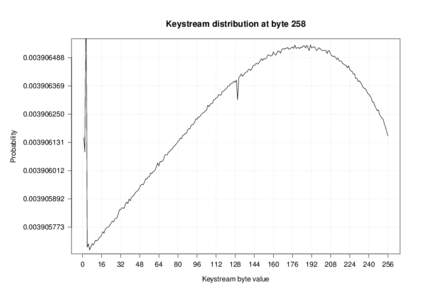 | Keystream distribution at byteDocID: 1xTZC - View Document |
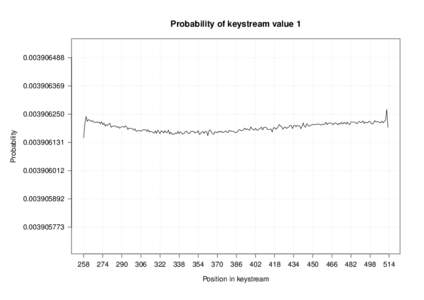 | Probability of keystream valueDocID: 1xTVG - View Document |
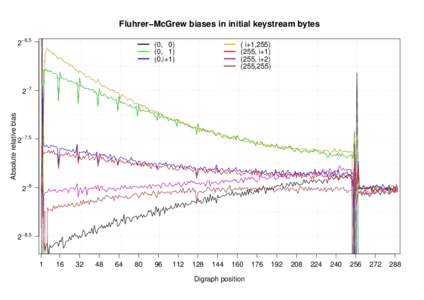 | Fluhrer−McGrew biases in initial keystream bytes 2−6.5 (0, 0) (0, 1) (0,i+1)DocID: 1xTHJ - View Document |
 | Biases in the RC4 keystream (128 bit uniform keys) Nadhem AlFardan and Dan Bernstein and Kenny Paterson and Bertram Poettering and Jacob Schuldt Royal Holloway, University of London University of Illinois at ChicagoDocID: 1tSaM - View Document |
 Intercepting GSM traffic Washington D.C., Feb 2008, Black Hat Briefing Abstract: This talk is about GSM security. We will explain the security, technology and protocols of a GSM network. We will
Intercepting GSM traffic Washington D.C., Feb 2008, Black Hat Briefing Abstract: This talk is about GSM security. We will explain the security, technology and protocols of a GSM network. We will