1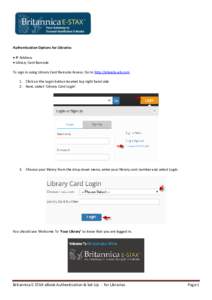 | Add to Reading ListSource URL: china.eb.comLanguage: English - Date: 2017-11-17 10:52:50
|
|---|
2 | Add to Reading ListSource URL: cdn1.esetstatic.comLanguage: English - Date: 2017-05-09 05:46:40
|
|---|
3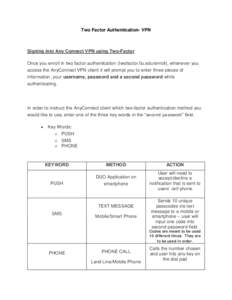 | Add to Reading ListSource URL: twofactor.fiu.edu- Date: 2017-01-24 14:17:16
|
|---|
4 | Add to Reading ListSource URL: netcom.army.mil- Date: 2009-10-26 18:13:04
|
|---|
5 | Add to Reading ListSource URL: www.adi-mps.com- Date: 2016-01-27 00:15:09
|
|---|
6 | Add to Reading ListSource URL: www.icscc.org- Date: 2016-06-12 05:12:23
|
|---|
7 | Add to Reading ListSource URL: csrc.nist.govLanguage: English - Date: 2016-08-01 15:13:29
|
|---|
8 | Add to Reading ListSource URL: www.inforouter.comLanguage: English - Date: 2015-03-26 12:13:27
|
|---|
9 | Add to Reading ListSource URL: www.zuv.fau.deLanguage: English - Date: 2015-08-04 03:58:15
|
|---|
10 | Add to Reading ListSource URL: ietf.orgLanguage: English - Date: 2014-03-02 06:27:58
|
|---|