731 | Add to Reading ListSource URL: www.scs.stanford.eduLanguage: English - Date: 2016-01-02 20:09:14
|
|---|
732 | Add to Reading ListSource URL: www.ee.hawaii.eduLanguage: English - Date: 2012-09-26 06:14:40
|
|---|
733 | Add to Reading ListSource URL: www.fox-it.comLanguage: English - Date: 2016-02-28 10:36:02
|
|---|
734 | Add to Reading ListSource URL: www.jhuapl.eduLanguage: English - Date: 2016-03-29 09:30:55
|
|---|
735 | Add to Reading ListSource URL: www.wtc7.netLanguage: English - Date: 2006-04-28 13:01:06
|
|---|
736 | Add to Reading ListSource URL: www.mitls.orgLanguage: English - Date: 2016-01-06 07:34:05
|
|---|
737 | Add to Reading ListSource URL: journalof911studies.comLanguage: English - Date: 2012-11-30 19:40:10
|
|---|
738 | Add to Reading ListSource URL: www.cs.technion.ac.ilLanguage: English - Date: 2001-12-17 04:15:54
|
|---|
739 | Add to Reading ListSource URL: journalof911studies.comLanguage: English - Date: 2012-07-01 08:21:10
|
|---|
740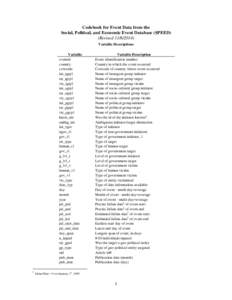 | Add to Reading ListSource URL: www.clinecenter.illinois.eduLanguage: English - Date: 2014-11-06 15:47:43
|
|---|