<--- Back to Details
| First Page | Document Content | |
|---|---|---|
 Date: 2011-06-07 17:51:22Crime prevention Brazilian Institute of Public Opinion and Statistics Surveillance Zogby Closed-circuit television Physical security Parking lot National Security Agency Security National security Public safety |
Add to Reading List |
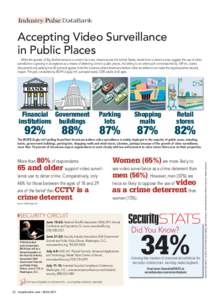
 Industry Pulse DataBank Accepting Video Surveillance in Public Places While the specter of Big Brother remains a concern for many citizens across the United States, results from a recent survey suggest the use of video
Industry Pulse DataBank Accepting Video Surveillance in Public Places While the specter of Big Brother remains a concern for many citizens across the United States, results from a recent survey suggest the use of video 



