1 | Add to Reading ListSource URL: www.sisudoc.orgLanguage: English - Date: 2017-06-20 16:04:09
|
|---|
2 | Add to Reading ListSource URL: www.oswego.eduLanguage: English - Date: 2016-02-05 13:37:21
|
|---|
3 | Add to Reading ListSource URL: www.sisudoc.orgLanguage: English - Date: 2017-06-20 13:43:57
|
|---|
4 | Add to Reading ListSource URL: www.louisianacure.org- Date: 2012-07-11 12:01:29
|
|---|
5 | Add to Reading ListSource URL: www.annabooks.com- Date: 2015-11-13 16:49:40
|
|---|
6 | Add to Reading ListSource URL: spcl.inf.ethz.chLanguage: English - Date: 2015-11-30 04:19:15
|
|---|
7 | Add to Reading ListSource URL: www.napcosecurity.comLanguage: English - Date: 2014-05-16 11:26:10
|
|---|
8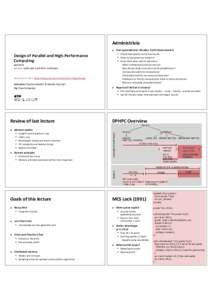 | Add to Reading ListSource URL: spcl.inf.ethz.chLanguage: English - Date: 2015-11-23 13:58:39
|
|---|
9 | Add to Reading ListSource URL: www.mpi-sws.orgLanguage: English - Date: 2013-12-03 05:32:06
|
|---|
10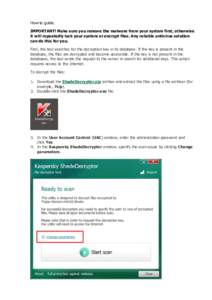 | Add to Reading ListSource URL: noransom.kaspersky.comLanguage: English - Date: 2016-07-25 08:15:55
|
|---|