<--- Back to Details
| First Page | Document Content | |
|---|---|---|
 Date: 2012-06-20 08:23:24Eli Biham NESSIE Symmetric-key algorithm Serpent Cryptographic hash function Boomerang attack Advanced Encryption Standard Cryptanalysis KASUMI Cryptography Block ciphers SHACAL |
Add to Reading List |
 | University of Illinois Healthcare Info Sessions: Questions & Answers The following questions were asked during three “town hall” Healthcare Information Sessions, as well as submitted via email to University Human ReDocID: 1ts1T - View Document |
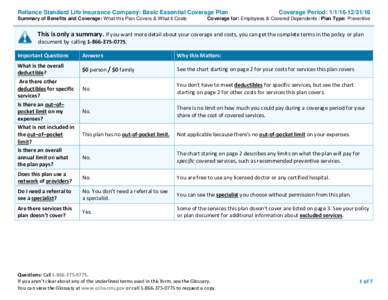 | Reliance Standard Life Insurance Company: Basic Essential Coverage Plan Summary of Benefits and Coverage: What this Plan Covers & What it Costs Coverage Period: Coverage for: Employees & Covered DependenDocID: 1t7Cu - View Document |
 | Statement of SURS Annuity StatusDocID: 1t62U - View Document |
 | Microsoft Word - SOEEA_Reporting_Policy_APCS_100608.docDocID: 1t5xI - View Document |
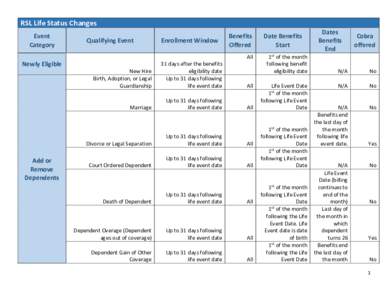 | RSL Life Status Changes Event Category Qualifying EventDocID: 1sWJt - View Document |
 Cryptographic Hash Workshop
Cryptographic Hash Workshop