<--- Back to Details
| First Page | Document Content | |
|---|---|---|
 Money laundering Financial regulation Tax evasion Property law Crime Economy Terrorism Asset forfeiture Proceeds of Crime Act National Crime Agency Financial crimes Suspicious activity report |
Add to Reading List |
 | Terms and conditions The Child Exploitation and Online Protection Centre is a command of The National Crime Agency. The National Crime Agency is part of the Crown. Thinkuknow is the CEOP Command’s Education programme fDocID: 1v9Aj - View Document |
 | PDF DocumentDocID: 1rpQ0 - View Document |
 | YOUR COUNTRY NEEDS YOU: HERE’S HOW TO ANSWER THE CALL! BRIGADIER GENERAL JOHN ADAMS, US ARMY (RET) & LIEUTENANT COLONEL CHRIS COURTNEY, US ARMY (RET)DocID: 1rkYm - View Document |
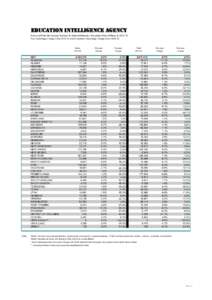 | EDUCATION INTELLIGENCE AGENCY Active and Total Membership Numbers for National Education Association State Affiliates forPlus Percentage Change Sinceand Cumulative Percentage Change SinceNEA ALDocID: 1rirI - View Document |
DOC DocumentDocID: 1r9Ik - View Document |
 Duties and responsibilities under POCA - second edition - September 2014
Duties and responsibilities under POCA - second edition - September 2014