<--- Back to Details
| First Page | Document Content | |
|---|---|---|
 Date: 2016-01-29 11:50:05Software Computing System software Computer access control Password Security Cryptography Pass Cryptographic software Challengeresponse authentication HTTP cookie Android |
Add to Reading List |
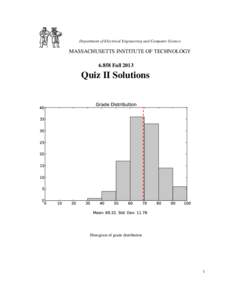
 Department of Electrical Engineering and Computer Science MASSACHUSETTS INSTITUTE OF TECHNOLOGYFallQuiz II Solutions
Department of Electrical Engineering and Computer Science MASSACHUSETTS INSTITUTE OF TECHNOLOGYFallQuiz II Solutions



