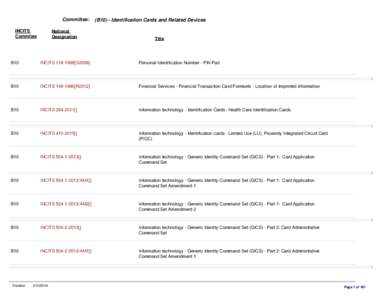
<--- Back to Details
| First Page | Document Content | |
|---|---|---|
 Date: 2015-01-24 06:51:50Access control Computing HID Global Radio-frequency identification Proximity card MIFARE Contactless smart card Smart card Magnetic stripe card Security Ubiquitous computing ISO standards |
Add to Reading List |
 Technology Basics White Paper How an HID Card is “Read” The purpose of this paper is to briefly explain the nature of the data on an HID card and the steps required to get that data to the controller and unlock a d
Technology Basics White Paper How an HID Card is “Read” The purpose of this paper is to briefly explain the nature of the data on an HID card and the steps required to get that data to the controller and unlock a d