<--- Back to Details
| First Page | Document Content | |
|---|---|---|
 Date: 2018-09-25 12:44:08Internet exchange point Routing Quagga Transmission Control Protocol Internet protocols Computing Email authentication Spam filtering Data transmission |
Add to Reading List |
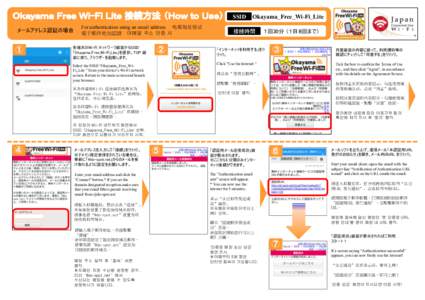 | SSID メールアドレス認証の場合 ① For authentication using an email address 电邮地址验证DocID: 1vbvF - View Document |
 | Introduction to Email Authentication An explanation of how SPF, DKIM, and DMARC function 2Q 2015DocID: 1s5Ss - View Document |
 | CUSTOMER PROTECT – RESPOND Your brand at risk Today, within a couple of minutes anyone can send an email claiming to be you. These phishing emails can leverage the domains you own, such as your YourCompany.com, or theyDocID: 1rrVL - View Document |
 | Why Johnny Still Can’t Encrypt: Evaluating the Usability of Email Encryption Software Steve Sheng Levi BroderickDocID: 1rrMN - View Document |
 Prof. Laurent Vanbever Networked Systems Group A test framework to verify end point implementations Semester thesis proposal
Prof. Laurent Vanbever Networked Systems Group A test framework to verify end point implementations Semester thesis proposal