<--- Back to Details
| First Page | Document Content | |
|---|---|---|
 Date: 2015-12-03 10:50:31Cryptography Cryptographic hash functions Hashing Applied mathematics Cryptocurrencies Public-key cryptography Cryptographic nonce SHA-2 Bitcoin Crypt Hash function Padding |
Add to Reading List |
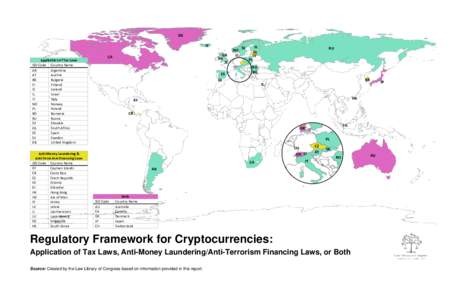 | Regulatory Framework for CryptocurrenciesDocID: 1xVKi - View Document |
 | Hijacking Bitcoin: Routing Attacks on Cryptocurrencies https://btc-hijack.ethz.ch Maria Apostolaki Aviv ZoharDocID: 1xVI1 - View Document |
 | review articles When it comes to anonymizing cryptocurrencies, one size most definitely does not fit all. BY DANIEL GENKIN, DIMITRIOS PAPADOPOULOS, AND CHARALAMPOS PAPAMANTHOUDocID: 1xUXr - View Document |
 | Hijacking Bitcoin: Routing Attacks on Cryptocurrencies https://btc-hijack.ethz.ch Maria Apostolaki Aviv ZoharDocID: 1xUq2 - View Document |
 | Algorand: Scaling Byzantine Agreements for Cryptocurrencies Yossi Gilad, Rotem Hemo, Silvio Micali, Georgios Vlachos, Nickolai Zeldovich MIT CSAIL ABSTRACTDocID: 1xUbv - View Document |
 The Politics of Cryptography: Bitcoin and The Ordering Machines
The Politics of Cryptography: Bitcoin and The Ordering Machines