191 | Add to Reading ListSource URL: css.csail.mit.eduLanguage: English - Date: 2016-01-29 11:50:05
|
|---|
192 | Add to Reading ListSource URL: www.greenbone.netLanguage: English - Date: 2016-06-16 08:24:26
|
|---|
193 | Add to Reading ListSource URL: ccdcoe.orgLanguage: English - Date: 2016-06-17 04:21:55
|
|---|
194 | Add to Reading ListSource URL: maecproject.github.ioLanguage: English - Date: 2016-06-15 18:10:07
|
|---|
195 | Add to Reading ListSource URL: wpsecurityworkshop.comLanguage: English - Date: 2016-05-14 22:10:06
|
|---|
196 | Add to Reading ListSource URL: ww2.cs.fsu.eduLanguage: English - Date: 2013-02-18 11:48:25
|
|---|
197 | Add to Reading ListSource URL: cybercoe.army.milLanguage: English - Date: 2015-12-23 08:19:14
|
|---|
198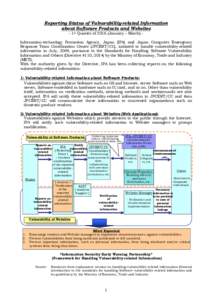 | Add to Reading ListSource URL: www.ipa.go.jpLanguage: English - Date: 2016-05-31 02:00:13
|
|---|
199 | Add to Reading ListSource URL: www.veracode.comLanguage: English - Date: 2016-01-20 16:34:29
|
|---|
200 | Add to Reading ListSource URL: www.deer-run.comLanguage: English - Date: 2004-08-16 11:51:23
|
|---|