<--- Back to Details
| First Page | Document Content | |
|---|---|---|
 Date: 2016-01-24 20:37:43Cryptography Computer security Logger Data Logfile Public-key cryptography Log analysis Trusted computing Disk encryption Trusted Platform Module |
Add to Reading List |
 | Florida Master Logger Continuing Logger Education (CLE) Training Requirements - 2018DocID: 1vo8v - View Document |
 | The LOGGER’S BARKRADIO CLUB of TACOMADocID: 1vdfS - View Document |
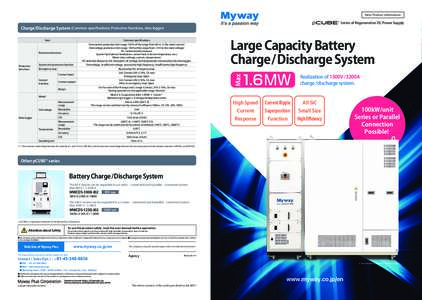 | New Product Information Ⓡ Series of Regenerative DC Power Supply Charge/Discharge System (Common specifications: Protective functions, data logger)DocID: 1vc04 - View Document |
 | 40R Starter Wind Data Logger PackageDocID: 1uNVO - View Document |
 | 16-CHANNEL LOGGER Preconfigured with server and SSD Complete System, Ready to Run • All you need to record Including server, logger and cabling.DocID: 1uN40 - View Document |
 Continuous Tamper-proof Logging Using TPM 2.0 Arunesh Sinha1 , Limin Jia1 , Paul England2 , and Jacob R. Lorch2 1 Carnegie Mellon University, Pittsburgh, Pennsylvania, USA
Continuous Tamper-proof Logging Using TPM 2.0 Arunesh Sinha1 , Limin Jia1 , Paul England2 , and Jacob R. Lorch2 1 Carnegie Mellon University, Pittsburgh, Pennsylvania, USA