21![arXiv:1404.3465v1 [cs.CR] 14 AprNetwork-on-Chip Firewall: Countering Defective and Malicious System-on-Chip Hardware Michael LeMay∗, Carl A. Gunter University of Illinois at Urbana-Champaign arXiv:1404.3465v1 [cs.CR] 14 AprNetwork-on-Chip Firewall: Countering Defective and Malicious System-on-Chip Hardware Michael LeMay∗, Carl A. Gunter University of Illinois at Urbana-Champaign](https://www.pdfsearch.io/img/0e8d83adda193ca7c5af8c3b82efbf65.jpg) | Add to Reading ListSource URL: sharps.orgLanguage: English - Date: 2014-06-20 15:53:16
|
|---|
22 | Add to Reading ListSource URL: www.redsocks.euLanguage: English - Date: 2018-08-06 04:35:01
|
|---|
23 | Add to Reading ListSource URL: web.engr.oregonstate.edu- Date: 2016-07-26 12:27:06
|
|---|
24 | Add to Reading ListSource URL: s3.eurecom.frLanguage: English - Date: 2018-08-15 14:28:52
|
|---|
25 | Add to Reading ListSource URL: www.s3.eurecom.frLanguage: English - Date: 2017-11-07 11:46:31
|
|---|
26 | Add to Reading ListSource URL: m.smithworx.comLanguage: English - Date: 2010-07-01 18:07:10
|
|---|
27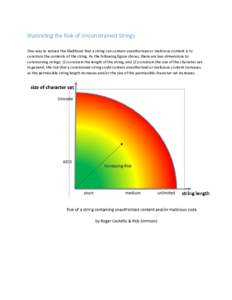 | Add to Reading ListSource URL: www.xfront.com- Date: 2017-03-08 13:42:08
|
|---|
28 | Add to Reading ListSource URL: web.cs.ucla.eduLanguage: English - Date: 2017-11-29 01:25:51
|
|---|
29 | Add to Reading ListSource URL: davidecanali.comLanguage: English - Date: 2013-09-25 18:20:21
|
|---|
30 | Add to Reading ListSource URL: people.cs.vt.eduLanguage: English - Date: 2012-04-20 15:19:52
|
|---|