41 | Add to Reading ListSource URL: www.kapravelos.comLanguage: English |
|---|
42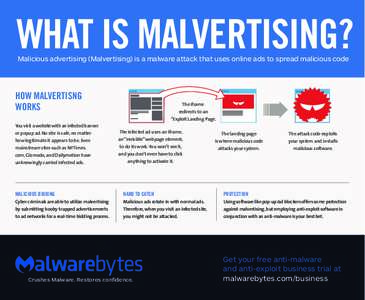 | Add to Reading ListSource URL: fr.malwarebytes.comLanguage: English - Date: 2016-05-10 22:50:01
|
|---|
43 | Add to Reading ListSource URL: digital-forensics.sans.orgLanguage: English - Date: 2017-10-25 19:33:13
|
|---|
44 | Add to Reading ListSource URL: www.av-comparatives.org- Date: 2013-01-25 05:18:13
|
|---|
45 | Add to Reading ListSource URL: d2oc0ihd6a5bt.cloudfront.net- Date: 2017-06-28 23:54:09
|
|---|
46 | Add to Reading ListSource URL: faculty.cse.tamu.edu- Date: 2017-05-09 12:05:41
|
|---|
47 | Add to Reading ListSource URL: www.rapid7.com- Date: 2016-11-08 14:15:05
|
|---|
48 | Add to Reading ListSource URL: www.measurementlab.net- Date: 2018-03-30 16:32:38
|
|---|
49 | Add to Reading ListSource URL: benjaminvandersloot.com- Date: 2018-03-26 16:16:53
|
|---|