51 | Add to Reading ListSource URL: info.publicintelligence.net- Date: 2017-06-18 21:47:47
|
|---|
52 | Add to Reading ListSource URL: info.publicintelligence.net- Date: 2016-09-11 19:09:27
|
|---|
53 | Add to Reading ListSource URL: eprint.iacr.org- Date: 2008-01-30 02:51:31
|
|---|
54 | Add to Reading ListSource URL: www.ics.forth.gr- Date: 2012-03-22 09:27:59
|
|---|
55 | Add to Reading ListSource URL: www.isti.tu-berlin.de- Date: 2014-02-06 14:25:05
|
|---|
56 | Add to Reading ListSource URL: faculty.cse.tamu.edu- Date: 2013-12-18 10:56:16
|
|---|
57 | Add to Reading ListSource URL: www.ndsl.kaist.edu- Date: 2013-10-03 11:10:54
|
|---|
58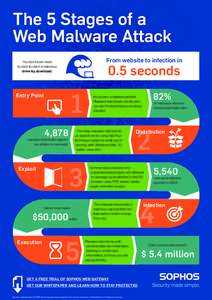 | Add to Reading ListSource URL: sophos.files.wordpress.com- Date: 2014-03-26 15:55:28
|
|---|
59 | Add to Reading ListSource URL: www.aha.org- Date: 2016-06-24 15:29:56
|
|---|