71 | Add to Reading ListSource URL: sec.cs.bham.ac.uk- Date: 2016-05-03 06:16:44
|
|---|
72 | Add to Reading ListSource URL: www.uvic.ca- Date: 2012-06-18 19:10:55
|
|---|
73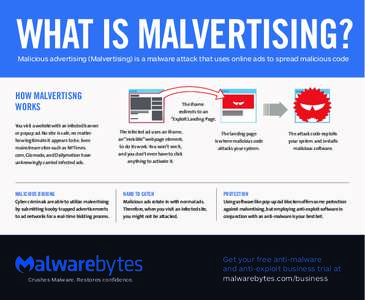 | Add to Reading ListSource URL: www.malwarebytes.com- Date: 2016-08-25 18:01:09
|
|---|
74 | Add to Reading ListSource URL: www.sandvine.com |
|---|
75 | Add to Reading ListSource URL: www.ll.mit.edu- Date: 2016-07-12 14:43:47
|
|---|
76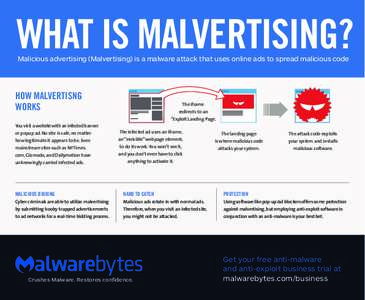 | Add to Reading ListSource URL: pt.malwarebytes.com- Date: 2016-05-10 23:14:53
|
|---|
77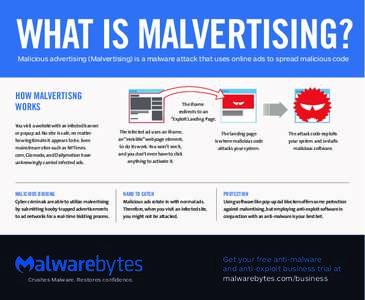 | Add to Reading ListSource URL: it.malwarebytes.com- Date: 2016-05-10 22:51:39
|
|---|
78 | Add to Reading ListSource URL: www.tc-communications.de- Date: 2015-12-21 08:31:42
|
|---|
79 | Add to Reading ListSource URL: esec-lab.sogeti.com- Date: 2016-07-01 12:08:46
|
|---|
80 | Add to Reading ListSource URL: www.wsbcs.net- Date: 2015-11-20 18:12:30
|
|---|