<--- Back to Details
| First Page | Document Content | |
|---|---|---|
 Date: 2016-04-21 07:36:03Computer access control Identity management Federated identity Identity documents Electronic authentication Public administration Multi-factor authentication FIPS 201 Authentication Password Privileged identity management Security token |
Add to Reading List |
 | CA Privileged Access Manager - Data SheetDocID: 1q2LL - View Document |
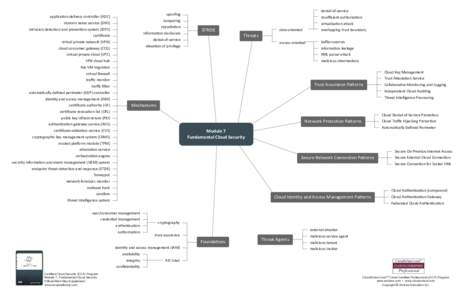 | denial-of-service spoofing application delivery controller (ADC)DocID: 1pdH5 - View Document |
 | Fischer Identity™ Turn Identity Management into a Strategic Advantage Privileged Access ManagementDocID: 1onIj - View Document |
 | Best Practices for Privileged User PIV AuthenticationDocID: 1noMI - View Document |
 | Fischer Identity™ Turn Identity Management into a Strategic Advantage Access TerminationDocID: 1jzSk - View Document |
 Best Practices for Privileged User PIV Authentication
Best Practices for Privileged User PIV Authentication