<--- Back to Details
| First Page | Document Content | |
|---|---|---|
 Date: 2007-12-19 09:22:01IEEE 802.11 Computer network security Secure communication Wired Equivalent Privacy RC4 Related-key attack IEEE 802.11i-2004 Fluhrer Mantin and Shamir attack CCMP Cryptography Wireless networking Cryptographic protocols |
 | Mr. Housley is the Founder of Vigil Security, LLC, and he is coauthor of “Planning for PKI” and “Implementing Email and Security Tokens” published by John Wiley & Sons. He has over 30 years of communications andDocID: 1qoXX - View Document |
November 2005 doc.: IEEE1205r0 IEEE P802.11 Wireless LANs IEEEWorking Group Comments on 1N7904 Date:DocID: 1pZvC - View Document | |
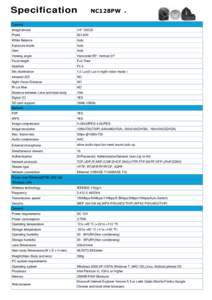 | PDF DocumentDocID: 1pGHQ - View Document |
 | I N T U I C O M BroadBand Solutions 4.9GHzGHz BROADBAND SPECIFICATIONS K E Y F E AT U R E SDocID: 1oPrz - View Document |
 | Connecting to the Rovernet WPA2 Secured Wireless Network with the Mac OS XLeopard) Configuring your wireless device to use WPA2 takes a few minutes. You will, however, need to meet the following system requirementDocID: 1o0if - View Document |
