<--- Back to Details
| First Page | Document Content | |
|---|---|---|
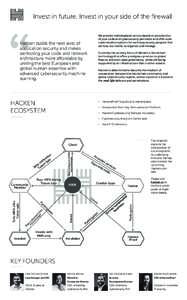
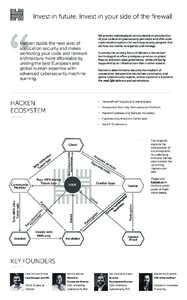
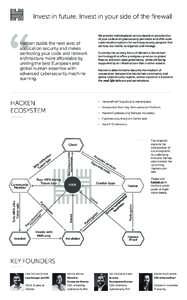
 Date: 2006-06-19 12:19:40Software development Software development process Extreme programming Agile software development Software requirements Software testing Extreme programming practices User story Acceptance testing XP INVEST Requirement |
Add to Reading List |
 Microsoft PowerPoint - XP.ppt
Microsoft PowerPoint - XP.ppt