1 | Add to Reading ListSource URL: www.jesuswordsonly.comLanguage: English - Date: 2009-05-12 19:55:50
|
|---|
2 | Add to Reading ListSource URL: www.normalesup.orgLanguage: English - Date: 2014-11-18 09:13:09
|
|---|
3 | Add to Reading ListSource URL: danielhausknecht.euLanguage: English - Date: 2018-09-22 05:15:36
|
|---|
4 | Add to Reading ListSource URL: gdac.uqam.caLanguage: English - Date: 2017-10-04 00:22:29
|
|---|
5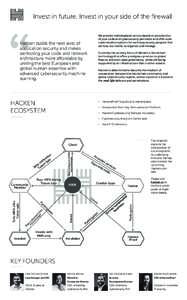 | Add to Reading ListSource URL: hacken.ioLanguage: English - Date: 2017-10-12 11:58:38
|
|---|
6 | Add to Reading ListSource URL: wexarts.orgLanguage: English - Date: 2018-04-20 16:23:07
|
|---|
7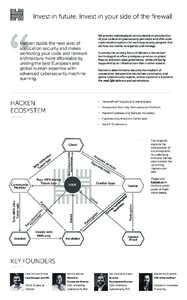 | Add to Reading ListSource URL: hacken.ioLanguage: English - Date: 2017-10-12 11:58:32
|
|---|
8 | Add to Reading ListSource URL: www.citibank.com.hkLanguage: English |
|---|
9 | Add to Reading ListSource URL: www.agaportal.deLanguage: English - Date: 2018-08-03 02:09:12
|
|---|
10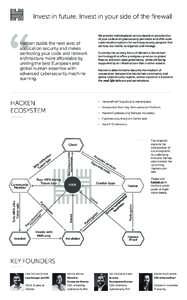 | Add to Reading ListSource URL: hacken.ioLanguage: English - Date: 2017-10-05 12:05:10
|
|---|