61 | Add to Reading ListSource URL: www.rfidblog.org.uk- Date: 2010-06-30 06:25:06
|
|---|
62 | Add to Reading ListSource URL: netecon.seas.harvard.eduLanguage: English - Date: 2009-11-30 14:32:02
|
|---|
63 | Add to Reading ListSource URL: www.shenandoah.co.lib.va.usLanguage: English - Date: 2015-10-28 16:47:20
|
|---|
64 | Add to Reading ListSource URL: www.missouriodyssey.orgLanguage: English - Date: 2015-12-28 00:24:08
|
|---|
65 | Add to Reading ListSource URL: www.conlog.co.zaLanguage: English - Date: 2015-11-26 07:18:35
|
|---|
66 | Add to Reading ListSource URL: www.emeraldgrouppublishing.comLanguage: English - Date: 2015-11-25 03:54:07
|
|---|
67 | Add to Reading ListSource URL: www.winlab.rutgers.eduLanguage: English - Date: 2013-04-18 23:09:49
|
|---|
68 | Add to Reading ListSource URL: www.ianacg.orgLanguage: English - Date: 2015-02-06 01:41:13
|
|---|
69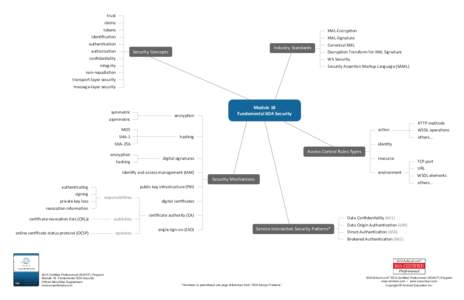 | Add to Reading ListSource URL: www.soaschool.comLanguage: English - Date: 2013-01-08 15:17:27
|
|---|
70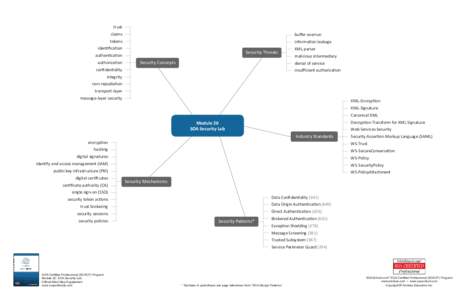 | Add to Reading ListSource URL: www.soaschool.comLanguage: English - Date: 2013-01-08 15:17:40
|
|---|