<--- Back to Details
| First Page | Document Content | |
|---|---|---|
 Date: 2013-09-06 09:56:55System software Computing Software Hypervisor Trusted Computing Protection ring Hardware virtualization Operating system Virtualization Malware Embedded hypervisor Qubes OS |
Add to Reading List |
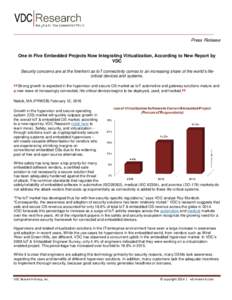 | Press Release One in Five Embedded Projects Now Integrating Virtualization, According to New Report by VDC Security concerns are at the forefront as IoT connectivity comes to an increasing share of the world’s lifecritDocID: 1qGfV - View Document |
 | Microsoft Word - Weber_Weber_Virtualisation_EnglishDocID: 1qxbL - View Document |
 | White Paper∗ Protecting e-Government Against Attacks Gernot Heiser University of New South Wales Sydney, AustraliaDocID: 1qno4 - View Document |
 | Definable functions continuous on curves in o-minimal structuresDocID: 1pqqs - View Document |
 | VirtualPower: Coordinated Power Management in Virtualized Enterprise Systems Ripal Nathuji Karsten SchwanDocID: 1plVv - View Document |
 Microsoft Word - Weber_Weber_Virtualisation_English
Microsoft Word - Weber_Weber_Virtualisation_English