<--- Back to Details
| First Page | Document Content | |
|---|---|---|
 Date: 2011-12-28 16:45:38Tunneling protocols Point-to-Point Tunneling Protocol Internet protocols Internet Standards Virtual private networks Computer network security Layer 2 Tunneling Protocol Point-to-Point Protocol daemon |
Add to Reading List |
 | Attacking the IPsec Standards in Encryption-only Configurations Jean Paul Degabriele1 and Kenneth G. Paterson2 ?DocID: 1rtuL - View Document |
 | In‐band Network Telemetry (INT) June 2016 Changhoon Kim, Parag Bhide, Ed Doe: DocID: 1rblj - View Document |
 | Secure Business Connectivity HOBLink VPN 2.1 Gateway The VPN Solution for More Security and Greater Flexibility Edition 10|13DocID: 1qYGD - View Document |
 | PDF DocumentDocID: 1qWA4 - View Document |
 | Enabling Data Center SDN with Stateless Source Routing Nathan&Farrington&ECOC,&Valencia,&SpainDocID: 1qI57 - View Document |
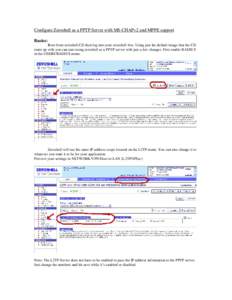
 Microsoft Word - Configure PPTP Server.doc
Microsoft Word - Configure PPTP Server.doc