1 | Add to Reading ListSource URL: sqrrl.comLanguage: English - Date: 2016-04-01 17:08:54
|
|---|
2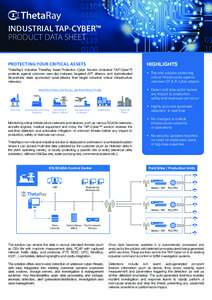 | Add to Reading ListSource URL: www.thetaray.comLanguage: English - Date: 2014-12-06 20:00:27
|
|---|
3 | Add to Reading ListSource URL: www.qosmos.comLanguage: English - Date: 2015-03-31 11:08:00
|
|---|
4 | Add to Reading ListSource URL: www.mcafee.comLanguage: English - Date: 2015-05-05 14:02:43
|
|---|
5 | Add to Reading ListSource URL: www.hp.comLanguage: English - Date: 2008-04-30 18:54:17
|
|---|
6![Deploying Statistical Anomaly Detection to Improve Cyber Security Dr. Greg Shannon Chief Scientist [removed] Deploying Statistical Anomaly Detection to Improve Cyber Security Dr. Greg Shannon Chief Scientist [removed]](https://www.pdfsearch.io/img/aad23071b5d70dba1ff0b29e1e71015b.jpg) | Add to Reading ListSource URL: www.ioc.ornl.govLanguage: English - Date: 2009-01-21 12:09:36
|
|---|
7 | Add to Reading ListSource URL: www.securonix.comLanguage: English - Date: 2012-04-04 12:33:39
|
|---|
8 | Add to Reading ListSource URL: www.mcafee.comLanguage: English - Date: 2014-01-10 01:04:53
|
|---|
9 | Add to Reading ListSource URL: www.lancope.comLanguage: English - Date: 2011-05-13 03:00:00
|
|---|